Configuring GitHub Actions Connection Details
Calibo Accelerate supports GitHub Actions for creating CI/CD workflows directly from the platform for deploying web and API technologies to Kubernetes clusters on AWS (EKS) and Azure (AKS), using GitHub repositories as the source.
Note:
GitHub Actions integration with the Calibo Accelerate platform currently supports only web and API technologies in Kubernetes deployment mode with GitHub as a source code repository. Support for Data technologies and Docker deployment mode will be introduced in future releases.
Before you configure the connection details of your GitHub Actions account in the Calibo Accelerate platform, ensure that you have completed the following prerequisites:
Note:
Calibo Accelerate uses organization-level secrets to securely manage credentials and configurations required for CI/CD automation. If you are working with private repositories, ensure that your GitHub subscription plan supports using organization secrets in private repositories.
GitHub Free and certain legacy plans do not allow organization secrets to be used in private repos. In such cases, deployment via GitHub Actions will not work as expected.
To avoid issues during pipeline execution, verify that your GitHub organization is on a plan (such as GitHub Team or Enterprise) that enables organization-level secrets for private repositories.
For more details, see GitHub documentation on managing organization secrets.
Mandatory GitHub Permissions for Workflow Automation
To enable seamless integration between Calibo Accelerate and GitHub Actions, a Personal Access Token (PAT) with specific permission scopes is required. The selected scopes grant Calibo the necessary access to manage repositories, trigger and monitor workflows, handle packages, and interact with organization or enterprise-level settings in GitHub. The following table outlines the required scopes and their purpose within the CI/CD pipeline.
|
Scope |
Sub-scope (if applicable) |
Description |
Why It's Required in Calibo Accelerate |
|---|---|---|---|
|
repo |
(full control) |
Grants access to all repo-related scopes |
Base permission for accessing private repositories required for code checkout, CI/CD triggers, and deployment actions. |
| repo:status | Access commit statuses | Required to fetch and update CI build/test status linked to commits and PRs. | |
| repo_deployment | Access deployment statuses | Enables Calibo to create, monitor, and update deployment events for GitHub Actions. | |
| public_repo | Access public repositories | Allows interaction with public repositories if your workflows or dependencies are hosted there. | |
| repo:invite | Accept repository invitations | Required if the Calibo GitHub app or token needs to accept repo invitations automatically (for example, shared orgs). | |
| security_events | Read security events | Allows visibility into security alerts tied to code for example, dependency vulnerabilities) that may affect build or deployment. | |
|
workflow |
– |
Manage GitHub Actions workflows |
Enables Calibo to trigger, monitor, and manage CI/CD workflows for deployments. |
|
write:packages |
– |
Upload packages to GitHub Package Registry |
Enables publishing build artifacts as packages to GitHub Package Registry. |
|
read:packages |
– |
Download packages from GitHub Package Registry |
Allows CI/CD pipelines to consume packages. |
|
delete:packages |
– |
Delete packages from GitHub Package Registry |
Used for cleanup of outdated or failed package versions. |
|
admin:org |
write:org |
Modify org/team membership |
Required to assign team-based access or manage team ownership during repo operations. |
|
manage_runners:org |
Manage self-hosted runners at the org level |
Needed when using self-hosted runners within GitHub Enterprise for workflow execution. |
|
|
notifications |
– |
Access user notifications |
May be used to notify users of status or updates related to workflow runs (optional, but enabled). |
|
user |
read:user |
Read all user profile data |
Allows Calibo to fetch user metadata tied to the GitHub token for validation and traceability. |
|
user:follow |
Follow and unfollow users |
Not critical for CI/CD but may be auto-checked when read:user is selected. |
|
|
delete_repo |
– |
Delete repositories |
Enables removal of temporary or test repositories created via automation. |
|
admin:enterprise |
manage_runners:enterprise |
Manage enterprise runners and runner groups |
Required for organizations that use GitHub Enterprise runners centrally. |
|
manage_billing:enterprise |
Manage billing settings at the enterprise level |
Enables Calibo admins to manage quota or usage limits if needed. |
|
|
read:enterprise |
Read enterprise profile data |
Fetches enterprise metadata for configuration validation. |
|
|
scim:enterprise |
SCIM provisioning of users and groups |
Required if Calibo handles user provisioning/integration with GitHub Enterprise via SCIM. |
|
|
audit_log |
read:audit_log |
Read access to audit logs |
Allows tracking of changes and events performed via Calibo on GitHub (security/compliance). |
|
codespace |
codespace:secrets |
Manage secrets for GitHub Codespaces |
If Codespaces are used in workflows, secrets must be managed programmatically. |
|
project |
read:project |
Read access to project boards |
Required if workflows are linked to project boards or GitHub Projects for tracking. |
To automate the continuous integration, testing, and deployment of your applications by using GitHub Actions from within the Calibo Accelerate platform, you must provide the connection details of your active GitHub Actions user account as explained in the following steps:
-
Sign in to the Calibo Accelerate platform and click Configuration in the left navigation pane.
-
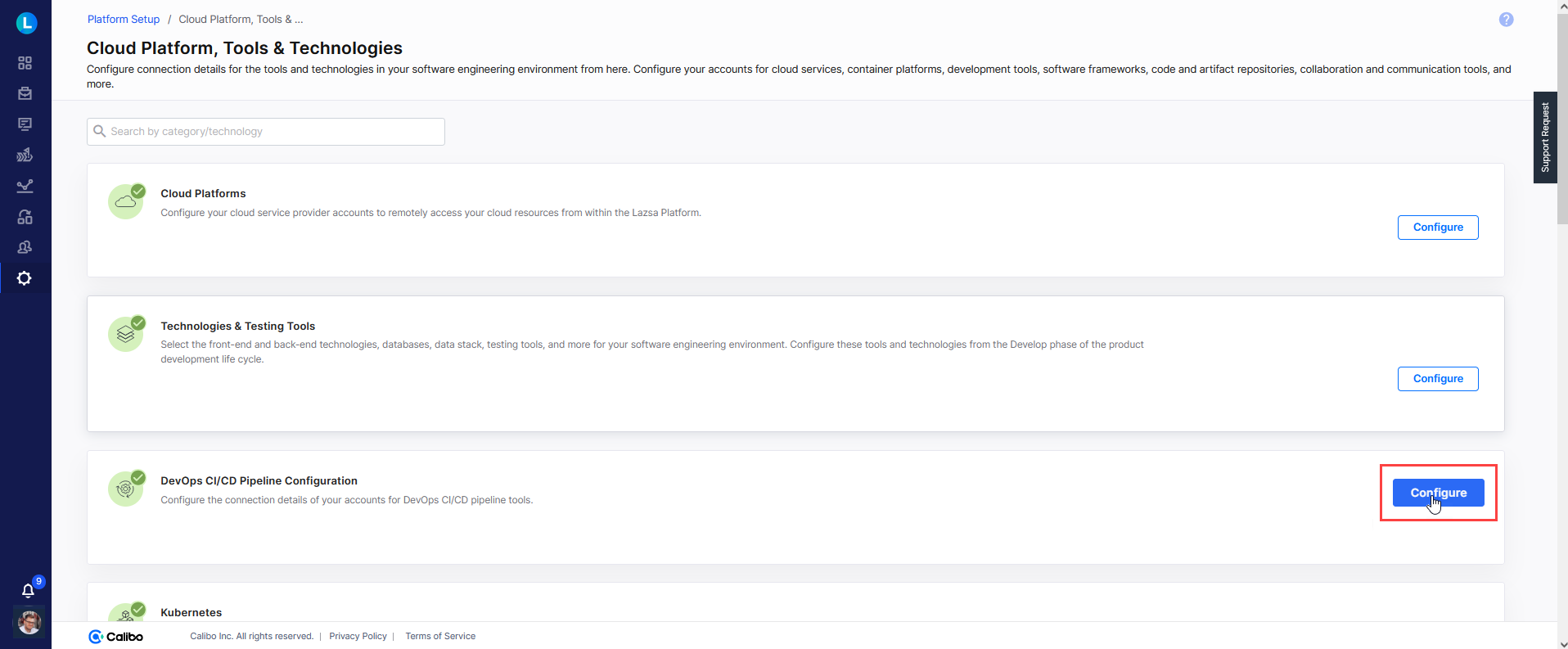
On the Platform Setup screen, on the Cloud Platform, Tools & Technologies tile, click Configure.
-
On the Cloud Platform, Tools & Technologies screen, in the DevOps CI/CD Pipeline Configuration section, click Configure.
(If you have already saved connection details for at least one CI/CD tool account, you see the Modify button here.)
-
On the DevOps CI/CD Pipeline Configuration screen, configure the appropriate connection based on the type of your GitHub repository.
-
Click GitHub Actions Cloud for repositories hosted on GitHub.com.
-
Click GitHub Actions Enterprise Server for self-hosted GitHub Enterprise instances.
-
-
For steps to configure the connection details of GitHub Actions Enterprise Server and GitHub Actions Cloud, refer to the respective sections below:
 GitHub Actions Enterprise Server
GitHub Actions Enterprise Server
-
To save the GitHub Actions Enterprise Server connection properties in Calibo Accelerate, do the following:
-
Configuration Name: Give a local name to this configuration. Your GitHub Actions Enterprise Server connection details are saved by this name in the Calibo Accelerate platform. This name helps you identify the connection when selecting a CI/CD tool during deployment stage configuration in Calibo Accelerate.
-
GitHub URL: Provide the URL of your GitHub Enterprise Server instance where your repositories are hosted and GitHub Actions workflows will run (for example, https://git.yourcompany.com).
-
Depending on how you want your GitHub credentials to be managed, do one of the following:
-
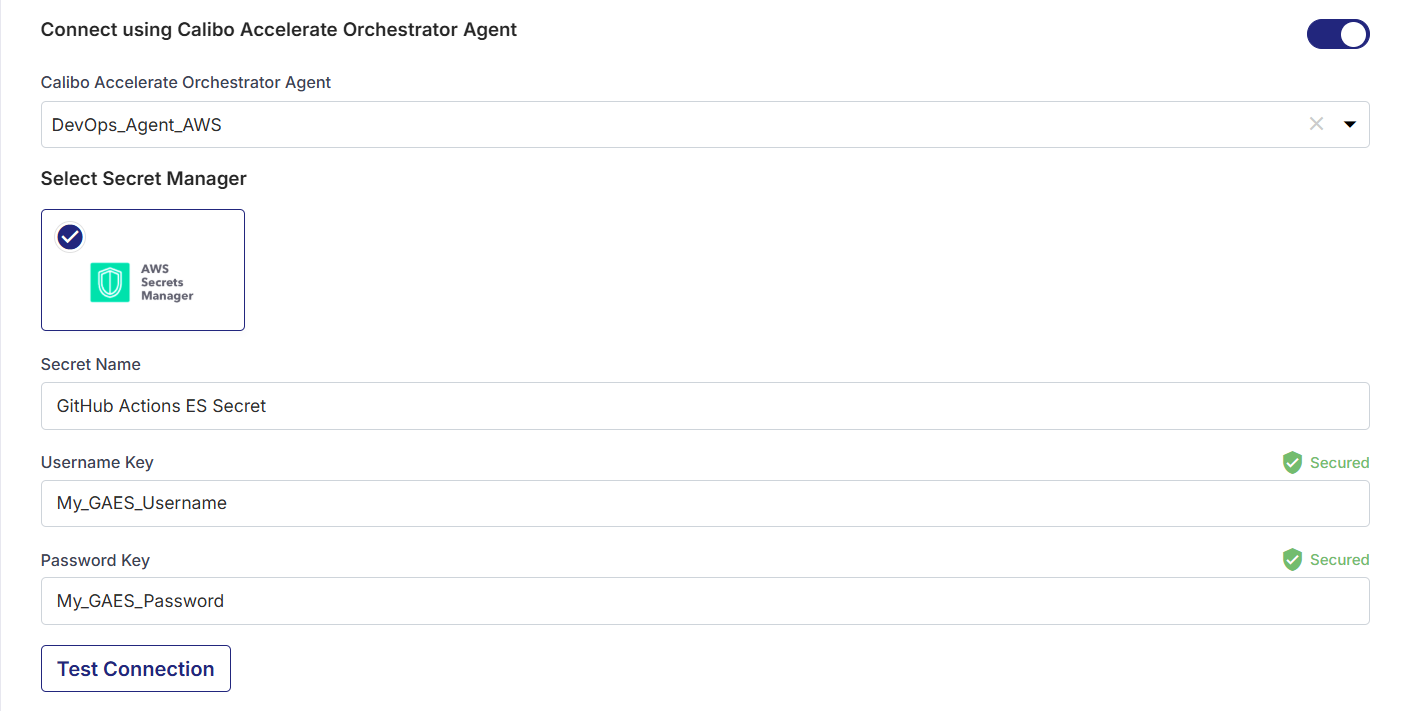
Connect using Calibo Accelerate Orchestrator Agent:
Turn on this toggle to use Calibo Accelerate Orchestrator Agent to programmatically resolve the GitHub credentials stored in your secrets management tool within your private network and to establish communication with your GitHub Enterprise Server.
In the Calibo Accelerate Orchestrator Agent dropdown list, all your configured agents are displayed. Select the one you want to use to connect to your GitHub Enterprise Server.
The secrets management tool (AWS Secrets Manager or Azure Key Vault) associated with the selected agent is auto-selected. Specify the details of GitHub secrets that the agent should retrieve from the secrets management tool.
-
For AWS Secrets Manager, provide the Secret Name, Username Key, and Password Key for your GitHub credentials, and then click Test Connection to verify connectivity to the GitHub Enterprise Server instance.
-
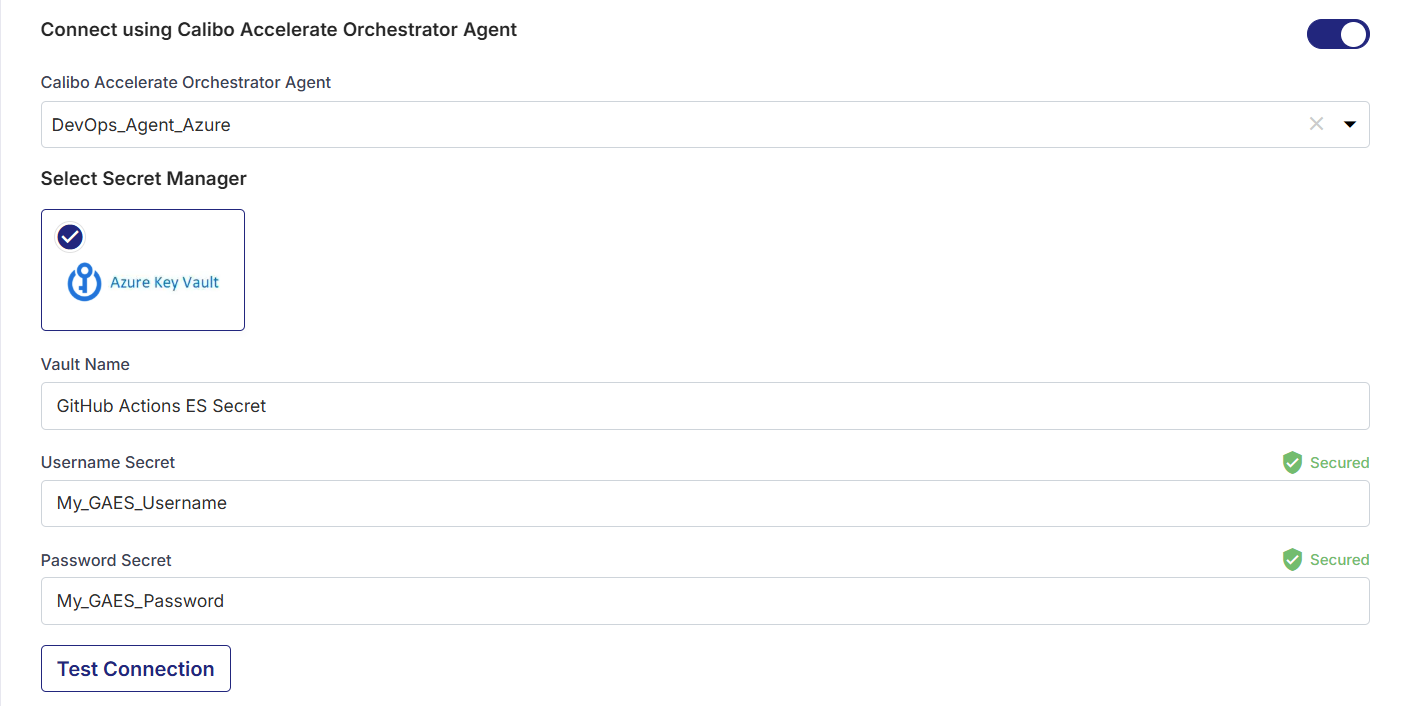
For Azure Key Vault, provide the Vault Name, Username Secret, and Password Secret for your GitHub credentials, and then click Test Connection to check whether you can connect to the configured GitHub instance successfully.
-
-
Select Secret Manager (If not using Orchestrator Agent)
If you don't use the Calibo Accelerate Orchestrator Agent, you can manually provide GitHub credentials, or retrieve them programmatically via your secrets management tool (such as AWS Secrets Manager or Azure Key Vault).
Do one of the following:
-
Option 1: Calibo Accelerate (built-in secrets store)
Select Calibo Accelerate and type your GitHub Username and Personal Access Token.
In this case, your GitHub credentials are securely stored in the Calibo-managed secrets store.
Then click Test Connection to check whether you can connect to the configured GitHub instance successfully.
-
Option 2: AWS Secrets Manager
Select AWS Secrets Manager. In the Secrets Management Tool dropdown list, the AWS Secrets Manager configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection.
Select your desired secrets management tool configuration.
Provide the Secret Name, Username Key, and the Password Key for the Calibo Accelerate platform to retrieve your GitHub Actions secrets.
Then click Test Connection to check whether you can connect to the configured GitHub instance successfully.
-
Option 3: Azure Key Vault
Select Azure Key Vault. In the Vault Configuration dropdown list, the Azure Key Vault configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection.
Select your desired secrets management tool configuration.
Provide the Vault Name, Username Secret, and Password Secret for the Calibo Accelerate platform to retrieve the credential values.
Then click Test Connection to check whether you can connect to the configured GitHub instance successfully.
-
-
-
Organization:
After you provide your GitHub credentials and fill in the other fields, the names of the organizations associated with your user account are fetched automatically. Choose your desired organization from the list of available organizations. By selecting the organization, you choose where repositories for each added technology should be created. Also, existing repositories from the selected organization can also be accessed through Calibo Accelerate.
- Secure configuration details with a password (Optional)
To restrict access to this connection configuration, enable the Secure configuration details with a password option, enter and confirm a password to secure the connection.This is optional but recommended. When you share the connection details with multiple users, password protection helps you ensure authorized access to the connection details.
-
After you save and activate the configured connection details, you can see your saved configuration listed in the DevOps CI/CD Pipeline Configuration section on the Cloud Platform, Tools & Technologies screen.
-
 GitHub Actions Cloud
GitHub Actions Cloud
To save the GitHub Actions Cloud connection properties in Calibo Accelerate, do the following:
-
Configuration Name: Give a local name to this configuration. Your GitHub Actions Cloud connection details are saved by this name in the Calibo Accelerate platform. This name will be used to identify the connection when selecting a CI/CD tool during deployment stage configuration in Calibo Accelerate.
-
GitHub URL: Provide the URL of your GitHub server where your repositories are hosted and your Actions workflows will run.
-
Depending on how you want your GitHub Actions credentials to be managed, do one of the following:
-
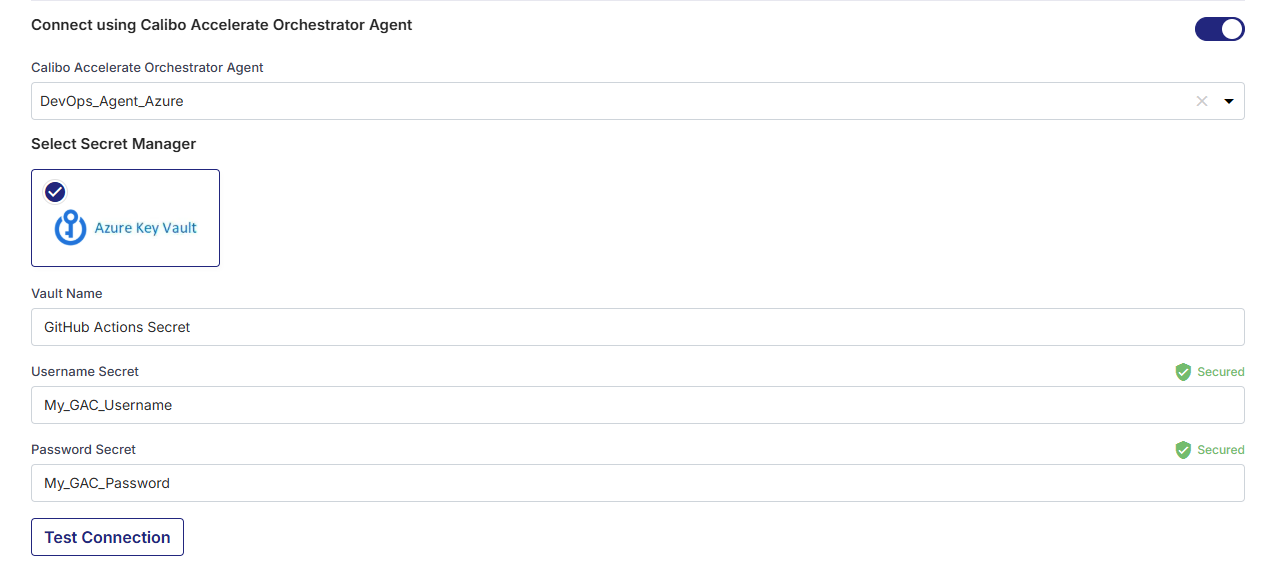
Connect using Calibo Accelerate Orchestrator Agent:
Turn on this toggle to use Calibo Accelerate Orchestrator Agent to programmatically resolve the GitHub credentials stored in your secrets management tool within your private network and to establish communication with your GitHub instance.
In the Calibo Accelerate Orchestrator Agent dropdown list, all your configured agents are displayed. Select the one you want to use to connect to your GitHub instance.
The secrets management tool that the selected Orchestrator Agent is authorized to access for retrieving secrets is auto-selected. Specify the details of GitHub secrets that the agent should retrieve from the secrets management tool. Currently, we support AWS Secrets Manager and Azure Key Vault.
For AWS Secrets Manager, provide the Secret Name, Username Key, and Password Key for your GitHub credentials, and then click Test Connection to check whether you can connect to the configured GitHub instance successfully.
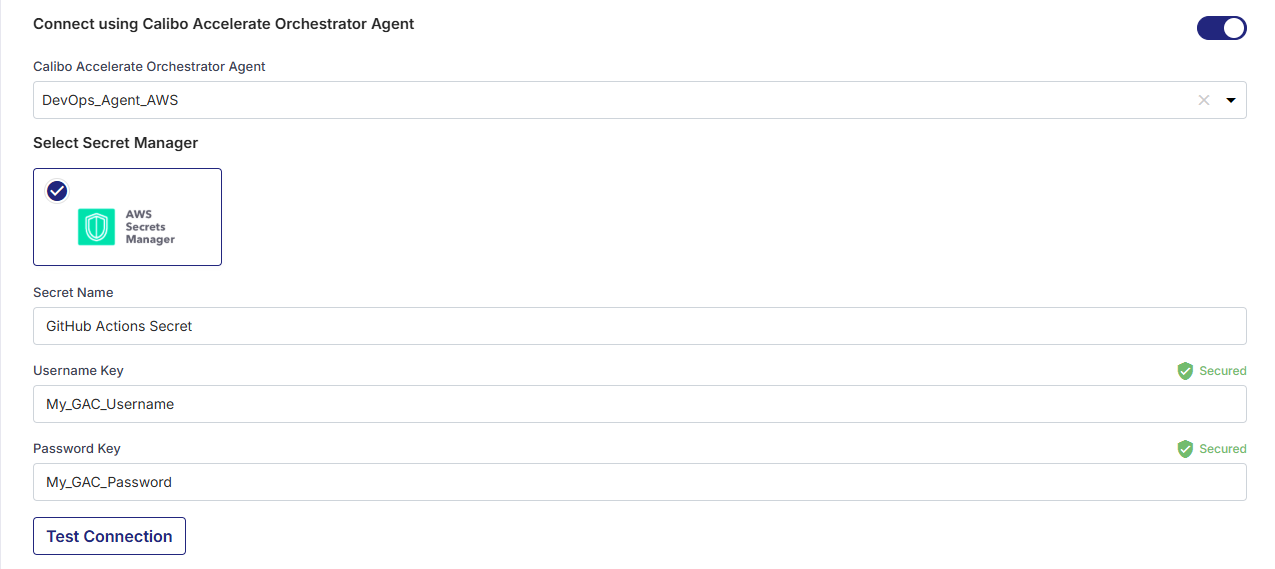
For Azure Key Vault, provide the Vault Name, Username Secret, and Password Secret for your GitHub credentials, and then click Test Connection to check whether you can connect to the configured GitHub instance successfully.
-
Select Secret Manager
If you don't use the Calibo Accelerate Orchestrator Agent, you can directly provide your GitHub username and password or authentication token in the configuration, or retrieve it programmatically from your secrets management tool (such as AWS Secrets Manager or Azure Key Vault). Do one of the following:
-
Select Calibo Accelerate and type your GitHub Username and Personal Access Token.
In this case, your GitHub credentials are securely stored in the Calibo-managed secrets store.
Then click Test Connection to check whether you can connect to the configured GitHub instance successfully.
-
Select AWS Secrets Manager. In the Secrets Management Tool dropdown list, the AWS Secrets Manager configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection.
Select your desired secrets management tool configuration.
Provide the Secret Name, Username Key, and the Password Key for the Calibo Accelerate platform to retrieve your GitHub Actions secrets.
Then click Test Connection to check whether you can connect to the configured GitHub instance successfully.
-
Select Azure Key Vault. In the Vault Configuration dropdown list, the Azure Key Vault configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection.
Select your desired secrets management tool configuration.
Provide the Vault Name, Username Secret, and Password Secret for the Calibo Accelerate platform to retrieve the credential values.
Then click Test Connection to check whether you can connect to the configured GitHub instance successfully.
-
-
-
Organization:
After you provide your GitHub Cloud credentials and fill in the other fields, the names of the organizations associated with your GitHub Cloud account are fetched automatically. Choose your desired organization from the list of available organizations. By selecting the organization, you choose where repositories for each added technology should be created. Also, existing repositories from the selected organization can also be accessed through Calibo Accelerate.

Note:
Calibo Accelerate uses organization-level secrets to securely manage credentials and configurations required for CI/CD automation. If you are working with private repositories, ensure that your GitHub subscription plan supports using organization secrets in private repositories.
GitHub Free and certain legacy plans do not allow organization secrets to be used in private repos. In such cases, deployment via GitHub Actions will not work as expected.
To avoid issues during pipeline execution, verify that your GitHub organization is on a plan (such as GitHub Team or Enterprise) that enables organization-level secrets for private repositories.
For more details, see GitHub documentation on managing organization secrets.
- Secure configuration details with a password
To password-protect your Jenkins account connection details, enable the Secure configuration details with a password option, enter a password, and then retype it to confirm.This is optional but recommended. When you share the connection details with multiple users, password protection helps you ensure authorized access to the connection details.
-
After you save and activate the configured connection details, you can see your saved configuration listed in the DevOps CI/CD Pipeline Configuration section on the Cloud Platform, Tools & Technologies screen.
-
With this, your connection details for GitHub Actions are successfully configured in the Calibo Accelerate platform. Now, you may want to configure the connection details of other tools involved in your PDLC.
| What's next? Configure Kubernetes Cluster Connection Details |